October is #CybersecurityAwarenessMonth! We are a proud partner with CISA (Cybersecurity & Infrastructure Security Agency) and the Secure Our World campaign. We will be sharing what you can do to keep our world more secure.
The third topic this month will be: Multifactor Authentication (MFA).
Your first thought may be…what is Multifactor Authentication and what do I need to do to set it up?
Multifactor authentication (MFA) is an account login process that requires multiple methods of authentication to verify a user’s identity for a login or other transaction. Multifactor authentication combines two or more independent credentials — what the user knows, such as a password; what the user has, such as a security token; and what the user is, by using biometric verification methods.
The goal of MFA is to create a layered defense that makes it more difficult for an unauthorized person to gain access to your accounts and data. If one factor is compromised or broken (such as your password), an attacker still has at least one or more barriers to breach before successfully breaking in and gaining access.
We will start with going over the Four Types of Multifactor Authentication.
One—SMS/Email:
Chances are, you’ve used one of these MFA methods before. SMS and email are the most popular types of multi-factor authentication around, as they’re notoriously simple and cost-effective.
- How it works: Both work by sending a time-sensitive passcode to your device, either via email or SMS message. The user must then access the passcode in their text messages or emails and enter it within the specified time to access their account. An attacker would need to enter the password and SMS/Email passcode to overcome this extra security measure, making accounts that much harder to breach.
- Pros and Cons: Customers and organizations prefer the simplicity of SMS and email-based MFA, as there’s no need for an authenticator, hardware, or app. The downside is that SMS and email-based MFA provide the least degree of security. For example, SMS messages can be cloned or hijacked by replacing a phone’s SIM card, and email-based passcodes can be overcome with brute-force attacks, just like a password.
Two—Authenticators:
While SMS and email-based MFA works by sending a passcode to your device, authenticators and push-button notifications send similar messages to your apps. The most common authenticators are Google Authenticator and Microsoft Authenticator, both of which can be downloaded for free on their respective app stores. Apple Authenticator is built into most newer devices, eliminating the need to download a specific app.
- How it works: First, users download the authenticator app onto their device. With each login attempt, the app will display a push-button notification. After opening the app, the user must verify their identity by entering a passcode or with a biometric scan.
- Pros and Cons: Users can often download authenticators for free, making them cost-effective MFA options. While the defense rate for this MFA can be high for certain cyber attacks, the extra steps can create MFA fatigue and dampen the user experience.
Three—Biometrics:
Biometrics recognizes your identity by information that’s unique to your body. Though it may be secure, there are concerns about it.
- How it works: Biometrics employs advanced technology to scan bodily features such as fingerprints, retinas, face, or voice. There’s also the option to leverage behavioral biometrics, which analyzes unique patterns in user actions like typing rhythm or mouse movements for continuous authentication.
- Pros and Cons: Biometric features are very difficult to duplicate, making them a highly secure MFA option. However, it’s possible to hijack fingerprints through latent fingerprinting or fake other biometrics with high-definition images that duplicate facial features with enough accuracy to breach an account.
Four—Security Keys:
A security token is a type of “Something you have” MFA. They involve some form of hardware, such as a YubiKey or SecurID, which are some of the most robust options.
- How it works: After entering their password, users must insert their key into a system that reads the digital code inside the hardware. Without the key, neither they nor an attacker can log in.
- Pros and Cons: Security keys are one of the most secure MFA options available, and because they’re physical devices, they can authenticate you even if you’re offline. However, users who lose them will be locked out of their system until they can set back up a new Security Key.
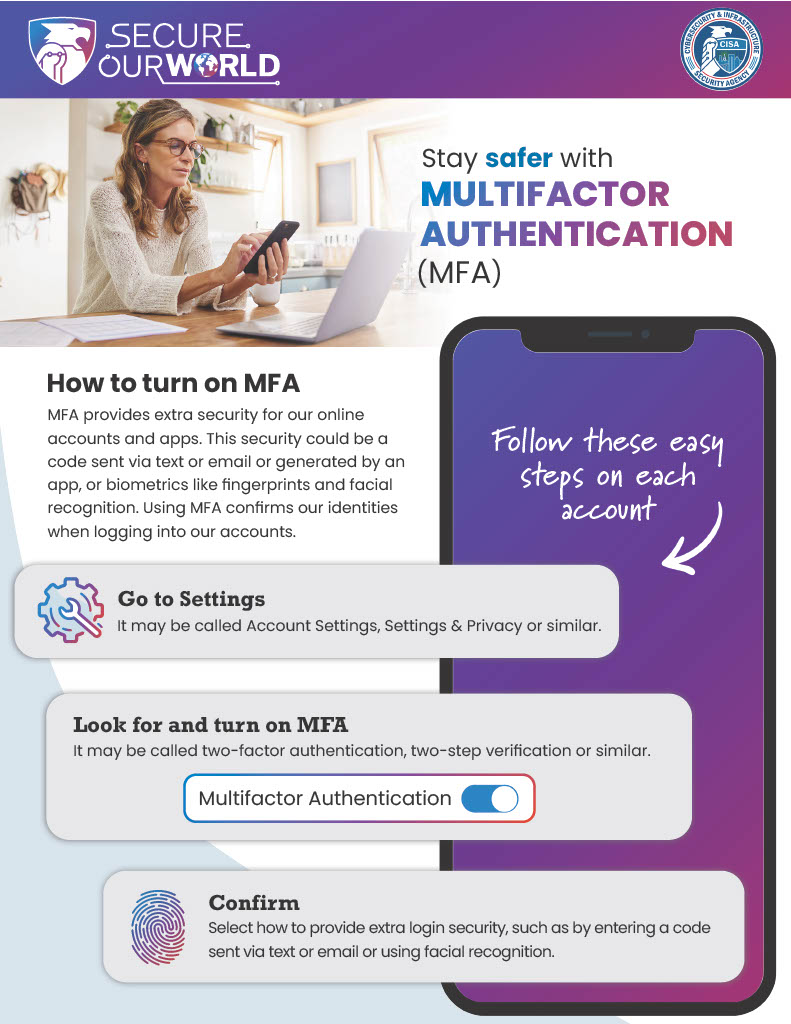
Now that you have a better understanding of Multifactor Authentication…it is time to set it up.
You will have to turn on MFA for each account or application. After you log in to each account or application, you will need to perform the following:
One—Go to Settings:
>>>It may be called Account Settings, Settings & Privacy or similar.
Two—Look for and turn on MFA.
>>>It may be called two-factor authentication, two step authentication or similar.
Three–Confirm:
>>>Select which MFA method to use from the options provided by each account or app. Examples are:
- Receiving a numeric code by text or email
- Using an authenticator app: These phone apps generate a new code every 30 seconds. Use this code to complete logging in.
- Biometrics: This uses our facial recognition, fingerprints, or voice to confirm our identities.
If you have any questions about the topic of Multifactor Authentication (MFA) OR with any other computer-related issues you may be having…just stop by our CONTACT US page and we’ll be more than happy to help you out.
If you would like to keep a copy of this Cybersecurity Newsletter…here is a link to open, download and print it out.